Best Practices for M&A Board Oversight. 9 Pitfalls That Create Deal Risk After the Term Sheet
Best Practices for M&A Board Oversight, so you spot 5 post-term-sheet pitfalls in tech, cyber, data, and regs, set gates, price risk, avoid surprises.


Once the term sheet is signed, the deal starts to feel like a train that's already left the station. Momentum rises, calendars tighten, and everyone wants to "keep things moving." That's exactly when shortcuts sneak in, especially around technology, cybersecurity, data, and regulatory risk. Those gaps rarely show up in the financial model until it's too late.
In plain terms, Best Practices for M&A Board Oversight means you're fulfilling the board's fiduciary duty, particularly its duty of care, by doing three things well: asking the right questions, setting clear decision gates, and making sure risk is priced, planned, and owned when evaluating deal momentum. You're not redoing management's work. You're making sure the board of directors ensures management's diligence is complete, comparable, and decision-ready.
Here's the hard truth. Many of the biggest deal risks live in systems you can't see in the P&L, like identity controls, data rights, incident readiness, and regulatory obligations tied to tech operations. These practices are central to effective strategic oversight and robust corporate governance. In the sections below, you'll walk through five common post term sheet pitfalls and what to do instead, so you protect value and close with confidence.
Key takeaways you can use in your next M&A board meeting
Set decision gates now: Agree on what must be true before signing final docs, not after.
Tie diligence to integration: Require every major risk to map to a funded integration action.
Confirm cyber and data risk in dollars: Ask for business impact, not only severity scores.
Validate the regulatory path: Make sure you understand approvals, timelines, and reporting duties.
Run one shared risk register as a core component of risk management: Assign one owner per risk, with dates, costs, and status.
Define walk-away triggers: Put them in writing, then control exceptions tightly.
Brief independent directors on significant walk-away triggers: Ensure they are informed to support informed oversight.
Name a single escalation path to ensure accountability: Decide how "bad news" reaches the board within 24 to 48 hours.
Set the board's oversight plan right after the term sheet
Right after the term sheet, the board of directors needs a simple oversight operating system to fulfill their role. Think of it like air traffic control. Planes can still land fast, but only if everyone uses the same rules.
Start with cadence. Weekly deal-risk updates work better than longer, less frequent briefings, because the facts change quickly. Next, require a dashboard that stays consistent week to week. If the format changes every time, bad news hides in the noise.
Decision gates come next. A gate is a board-level "pause point" tied to specific evidence through internal controls, not optimism. Ownership is the final piece. If risk belongs to "the team," it belongs to nobody.
You're not doing due diligence. You're ensuring management's due diligence produces clear decisions. If you want a model for translating security and tech risk into business language, the practical executive security and risk insights in https://tysonmartin.com/ciso-insights can help set the tone for board-ready reporting.
Each week, ask management to bring a short update that answers five questions, which the audit committee or equivalent group should review:
What are the top risks that could change valuation, timing, or closing conditions?
What diligence items are still open, and what could block answers?
What's changed in integration readiness, including people and vendors?
Where did the budget shift, and why?
What are the red flags you'd rather discuss now than explain later?
If the update doesn't include surprises, it might be hiding them.
Define decision gates and non-negotiables before the team falls in love with the deal
The most dangerous moment in M&A is when the story feels inevitable. At that point, "we'll fix it later" starts to sound reasonable. The board of directors' job is to set non-negotiables early to protect value, while objectivity still exists.
Common non-negotiables that often get missed include unresolved critical vulnerabilities that expose customer data, unclear ownership of key datasets (especially shared or licensed data), unknown regulatory exposure tied to how systems operate, major ERP or identity gaps that would break day-one access, and synergy timelines that assume miracles from integration teams.
Write walk-away triggers in plain language. Also name who can approve exceptions. Keep that group small, and require documented rationale. Otherwise, exceptions become the new plan.
Use one shared risk register that covers business, tech, cyber, and compliance
A good risk register is boring, and that's a compliment. It's a single source of truth with clear owners, due dates, mitigation cost, and a status that's either real or it's not.
Make one decision that saves weeks of confusion: separate deal-close risks from post-close risks. Deal-close risks affect valuation, legal terms, closing conditions, and timing. Post-close risks may still be serious, but they can be planned and funded after ownership transfers.
When risks tie directly to the integration plan, your board conversations get cleaner. You stop debating "is this bad," and start deciding "who owns it, what it costs, and when it's done."
The five post term sheet pitfalls that quietly add deal risk
These pitfalls don't look dramatic at first. They show up as small omissions, friendly assumptions, or a slide deck that feels "complete enough." Then the deal closes, and the real bill arrives.
Each pitfall below includes what it looks like in practice, why boards miss it, the damage it causes, and questions that surface it early. As you push for speed, keep one aim in mind: identifying material risks is the primary goal while building digital trust during high-stakes change requires clarity and accountability, not heroics. The perspective in https://tysonmartin.com/digital-trust-expert aligns well with how boards can govern trust when pressure is high.
Pitfall: treating tech and cybersecurity diligence as a paperwork exercise
It starts with comfort documents. A SOC 2 report, a pen test summary, and a policy binder show up. Everyone relaxes. Meanwhile, day-to-day reality stays untested.
Boards miss this because they confuse paperwork with effective cybersecurity oversight. The damage shows up after close: privileged access is messy, endpoint coverage is incomplete, shadow IT holds sensitive data, and incident response exists only as a document.
Ask questions that force reality:
"Show your top 10 technical and cyber risks with dollar impact."
"What would stop day-one operations, and how do we prevent it?"
"What is the plan for privileged access on close, including admins and service accounts?"
"Have we tested incident response with real people, not only a plan?"
A strong answer includes evidence, owners, and a timeline. A weak answer sounds like, "We're generally in good shape."
Pitfall: discovering data and privacy landmines after you commit to the price
Data risk often hides behind business success. A company can grow fast while collecting consent poorly, storing data too long, or moving it across borders without the right legal basis. Those issues don't always break the product. They do create regulatory and customer trust risk.
Boards miss this because "data" sounds abstract, and legal language feels distant from operations. The damage hits through remediation costs, delayed product plans, and restrictions on using acquired data for analytics or AI. Using acquired data in new ways can change your obligations overnight. Missing these landmines can lead to a breach of fiduciary duty and duty of loyalty.
Require one must-have deliverable: a plain-language data flow map, plus the top privacy risks and mitigations. Then ask:
"What customer data rights transfer with the deal, and what doesn't?"
"Where does data move across borders, and what approvals support that?"
"What's the data retention reality versus the written policy?"
"What new AI or analytics use cases are planned, and what would block them?"
If the map doesn't exist, you don't have control. You have guesses.
Pitfall: assuming integration will "figure it out" without a funded plan
This pitfall looks like optimism. "Integration is in progress," "IT is coordinating," "we'll rationalize tools later." The plan stays high level, and the budget stays vague.
Boards miss it because integration work is unglamorous, and teams avoid naming tradeoffs. The damage is predictable: duplicated tools, delayed migrations, weak controls, and burnout. Value leaks out through distractions, not only through breaches.
Insist on a 90-day integration plan with named owners, timeline, and budget. Also require a clear list of what will not be done in the first 90 days. That honesty protects focus. The business judgment rule protects directors who make informed, good-faith decisions based on these plans.
When capacity or experience is thin, you can stabilize risk and execution by bringing in https://tysonmartin.com/experienced-ciso-for-hire as experienced CISO leadership during the deal and early integration window.
Board questions that surface risk early:
"Who owns integration day-one access, and what's the fallback plan?"
"What's the integration budget delta versus the base case, and why?"
"Which security controls get stronger in the first 30 days, not later?"
Pitfall: missing third-party and supply chain exposure that follows the acquisition home
You don't just buy a company. You inherit its vendors, MSPs, offshore development partners, and embedded components inside products. Access paths multiply fast, especially when vendors hold admin credentials.
Boards miss this because vendor sprawl feels like procurement detail. The damage shows up as hidden contract risks, surprise renewals, weak security clauses, and unmanaged access that turns into an incident.
A practical approach works better than perfection:
Tier vendors by impact, then review the top tier first.
Pull the top contracts and confirm security and audit clauses.
Validate access paths, especially remote admin access and shared accounts.
Apply rapid controls for high-risk vendors (MFA, logging, least privilege).
Board questions that force clarity:
"Which five vendors could disrupt operations tomorrow if compromised?"
"Who outside the company has access to production, and how is it monitored?"
"Which vendor contracts change cost or terms after a change of control?"
Pitfall: letting governance drift, so red flags do not reach the board in time
Deal pressure breaks reporting. Teams get busy, metrics drift, and status updates turn into "green" stories. Escalation paths also blur, because nobody wants to be the person who slows the deal.
Boards miss this because updates still arrive on time. The damage is late discovery: a regulatory issue surfaces after commitments, a critical system fails during integration, or a known control gap turns into a real event. Late visibility hampers walk-away triggers under the Revlon standard or high-stakes defensive postures per the Unocal standard.
Set a "no surprises" rule, plus an escalation SLA. If a critical risk appears, management informs the deal lead and the board chair within 24 to 48 hours.
Keep the dashboard simple:
Open critical risks (count, trend, owners)
Budget variance
Milestones at risk
Control gaps that affect day-one operations
Regulatory items and due dates
A green dashboard with no debate is often a warning sign.
Turn oversight into action with a simple board level playbook
You don't need a thicker deck. You need repeatable board behaviors that keep speed without blind spots.
For the next 30 days, run a tight meeting rhythm: one standing deal-risk check-in each week, one deeper integration readiness review every two weeks, and one legal and regulatory checkpoint before any major contract step. Keep it short, keep it consistent, and keep the same dashboard format. Use board management software to maintain the dashboard and document decisions for transparency and disclosure.
To stay current as risk shifts, it helps to learn from leaders who treat education as part of the job. The perspective on https://tysonmartin.com/evolving-and-learning-ciso fits well when your board expects modern answers in changing risk environments.
Here's a simple deal readiness scorecard you can use to drive discussion:
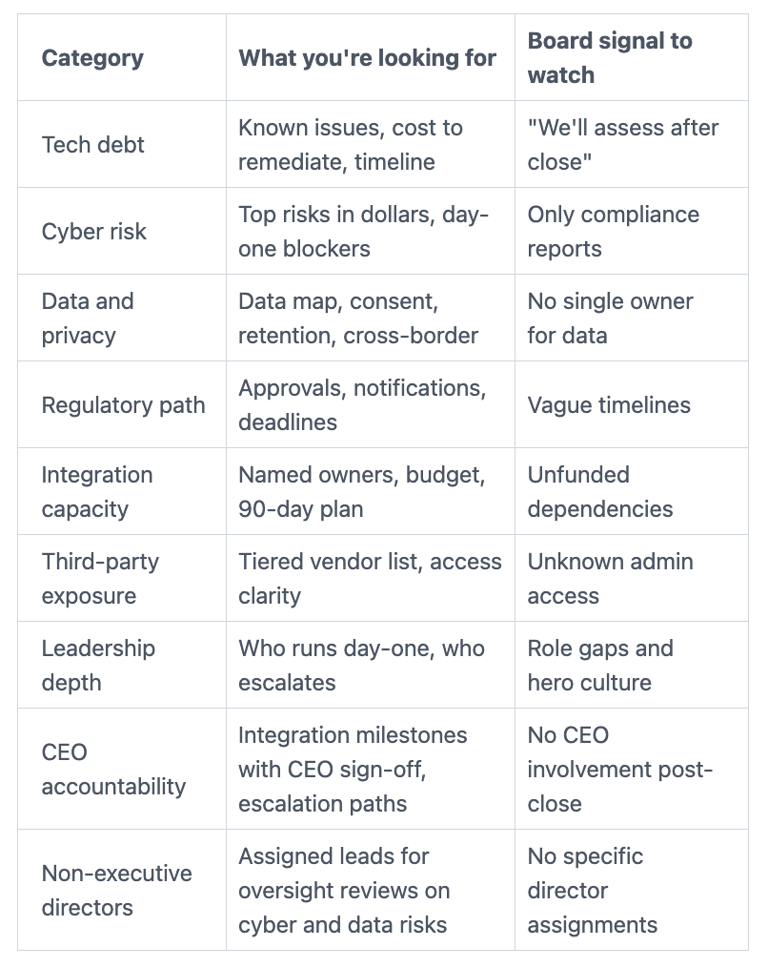
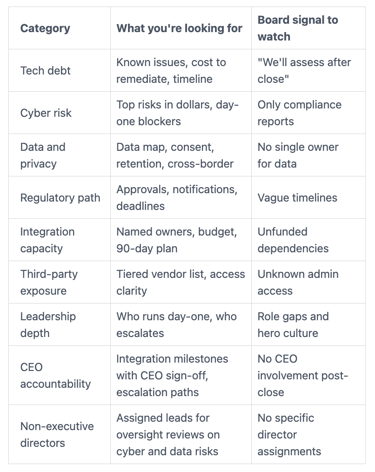
The exact questions to ask management, and what good answers sound like
Use questions that force tradeoffs, timing, and ownership:
"What are the top five risks that could change price or terms?"
"What would stop day-one operations, and what's the workaround?"
"Which systems must integrate first, and why?"
"What's the privileged access plan for close week?"
"Where is sensitive data stored, moved, and shared?"
"What regulatory obligations change after acquisition?"
"What's the 90-day integration plan, with budget and owners?"
"What's the vendor exposure, and who has admin access through vendors?"
"Which risks are close blockers versus post-close work?"
"What are your walk-away triggers, and who can approve exceptions?"
Example signals help you read the room fast:
For #1, strong: "Here are five risks, owners, dates, and dollar ranges." Weak: "Nothing major so far."
For #5, strong: "Here's the data flow map and top three privacy risks." Weak: "Legal is looking into it."
For #7, strong: "Here's the plan, plus what we won't do in 90 days." Weak: "Integration is underway."
When to bring in an independent advisor, and what to ask them to do
Bring in independent help when your in-house team lacks depth, the timeline is tight, you're in a regulated industry, the target has prior incidents, or the environment has heavy cloud and identity complexity.
Your advisor's scope should be clear: rapid risk review, validation of key management claims, an integration risk plan tied to funding, board-ready reporting that helps the audit committee assess the fairness opinion and identify any potential conflict of interest within management's reporting without hiding uncertainty.
If you need a clean way to start, focus on https://tysonmartin.com/engage-ciso-advisor for engaging a CISO advisor for board-ready guidance that fits your oversight cadence.
FAQs boards ask about deal risk after the term sheet
What should make you pause the deal?
Pause when you find unbounded risk with no owner or timeline, especially around identity, data rights, or regulatory exposure. Also pause when management can't explain day-one operations risk in plain terms.
How deep should cyber diligence go?
Deep enough to identify day-one blockers and top risks in dollars. Reports help, but you also need evidence of access controls, endpoint coverage, and incident readiness.
What is reasonable to fix pre-close?
Fix what could break day-one operations or create immediate legal exposure. Everything else needs a funded post-close plan with owners and dates.
How do you price tech debt?
Ask for a remediation estimate and the impact on integration timelines. Then reflect it in purchase price, escrow, reps and warranties, or integration budget.
Who owns risk post-close?
Name owners before close, not after. Each major risk should have a business owner and a technical owner, with one accountable executive.
How soon should you integrate identity and access?
As soon as you can do it safely. In most deals, access control is your fastest way to reduce breach risk and improve visibility.
How does M&A affect other board responsibilities?
M&A amplifies the need for stakeholder engagement to safeguard the company's reputation. Factor in succession planning and board composition to confirm the board has the right skills to oversee the new combined entity. Discuss deal-related performance evaluation during executive sessions to enable candid feedback.
What is the role of ESG reporting during integration?
Prioritize ESG reporting to track sustainability risks, ensure regulatory alignment, and demonstrate commitment to environmental, social, and governance standards in the merged operations.
Conclusion
After the term sheet, your job is to keep momentum without blind spots. You do that by treating oversight as a system, not a vibe. The Best Practices for MandA Board Oversight outlined here strengthen the organization's overall corporate governance.
You reduce risk when you stop treating cyber diligence as paperwork, when you map data and privacy before price hardens, when you fund integration instead of wishing for it, when you face third-party exposure early, and when you prevent governance drift so red flags surface fast. The board's strategic oversight relies on the work of independent directors and the accountability of the deal team to uphold strong corporate governance.
Use the playbook, set gates, demand clear owners, and escalate early. Maintaining high standards for transparency and disclosure and risk management when dealing with material risks is the hallmark of a high-functioning board, one that drives effective corporate governance with lasting impact.
If you want a benchmark for trusted leadership experience for high-stakes environments, review https://tysonmartin.com/certified-to-lead and align your expectations to that level of rigor.
